
Data
Cyber security: The basis for autonomous driving
Cyber security is of the utmost priority since the advent of digital, networked, and autonomous cars. Autonomous vehicles must fulfill these standards.
- Topics
- Digitization
- Data
- Cyber security
Three pillars of automotive security
Digitization is a key driver of innovation for companies and society. The permanent availability of networked and software-based systems, for example via the internet, is a key customer requirement that also applies to vehicle applications. These systems have the potential to create a wide range of additional vehicle services and functions. Thus, these functions have been increasing in number for years and are becoming an elementary component of the vehicle and the associated digital services, as corresponding functions are already offered by vehicle manufacturers today. In the future, the personalized range of functions offered by vehicles, infotainment equipment, and online services will represent an even larger percentage of the overall experience surrounding the vehicle. Automated driving will also become increasingly convenient due to the integration of external information, and further areas of application, such as driverless vehicles in urban environments, will be possible. Connected vehicles thus offer innovative features and functions that will make driving and the travel experience safer, more enjoyable, and more fascinating.
Back-end security
Back-end refers to the part of a software application that runs on the server and manages the data.
However, greater networking and additional interfaces and functionalities increase the attractiveness of an attack on vehicles and the connected infrastructure by hackers with different motivations. Also, because of the increasing degree of automation, it is necessary to protect corresponding vehicle functions against manipulation by way of security measures. To meet customer demands for networking and functionality in the digital age, appropriate security concepts are needed that provide sufficient overarching protection for vehicles, their connected back-end systems, and customer devices.
The aim here is to protect both vehicle and user data against unauthorized access, and any vehicle functions against manipulation. Automotive security thus covers both the data protection interests of customers (privacy) and the vehicle, its parts, and its functioning (safety). It is in the prime interest of the automotive industry to ensure the highest safety standards so as to protect the vehicle in the best possible way.
The automotive industry has recognized these security requirements and is investing accordingly in the development and protection of its products to meet the demands. Security measures are anchored in the following three pillars over the entire life cycle of the vehicle.
This position of the German Association of the Automotive Industry (VDA) is an extension of the existing VDA positions on "Data Protection" and "Access to the Vehicle and to Data Generated in the Vehicle."
1. Security engineering
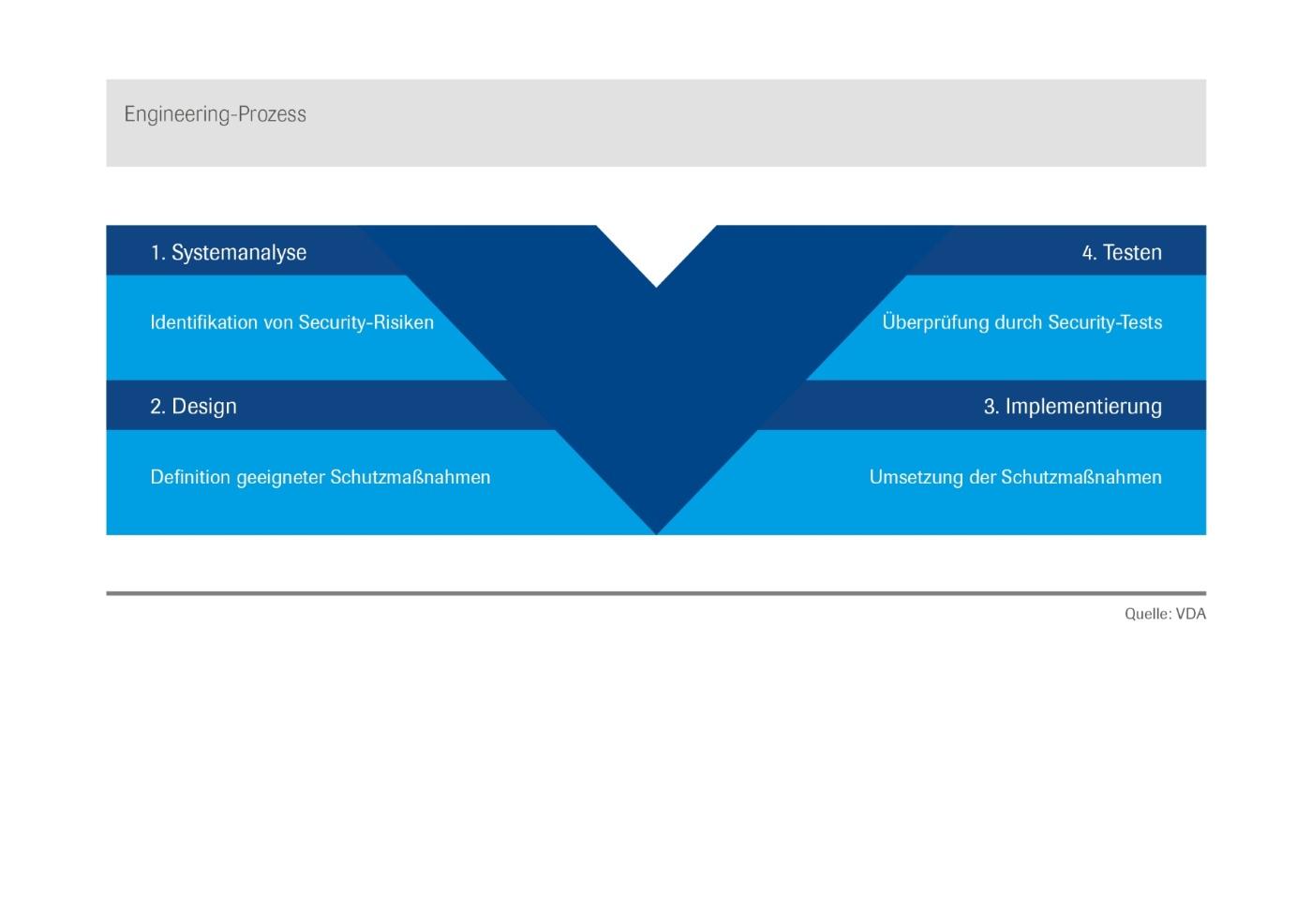
To ensure an adequate level of automotive security protection for new products, a uniform methodical procedure for the development of vehicle systems and their networking is being drawn up and applied in industry. This procedure includes the following process steps:
1. Identify and evaluate security risks
2. Define suitable measures for risk mitigation
3. Ensure and verify implementation of the measures
4. Test and approve the implementation
Engineering process
SAE International, formerly the Society of Automotive Engineers (SAE), is a non-profit organization for science and technology devoted to advancing mobility technologies.
A similar approach has already proved is worth in the form of ISO 26262 for functional security. Similarly, the VDA and its member companies have launched a standardization for automotive security engineering. With regard to global developments, a joint working group has been established with the standardization organizations ISO and SAE to draw up ISO-SAE AWI 21434 Road Vehicles – Cybersecurity Engineering. This standard creates a basis for turning the goals of automotive security into a uniform component of the entire development process in the automotive industry. The relevant aspects for product definition, design, implementation, and testing are covered by this standard, yet it does not prescribe any specific technology.
From the perspective of the automotive industry, this standard achieves a universal, consistent, application-related, and risk-adjusted understanding of security by design in product development and along the entire supply chain.
2. Basic technical requirements
A further pillar in the holistic approach to automotive security is basic technical requirements for security protection mechanisms and cryptographic processes. These basic requirements are built on international recommendations and standards, and are adapted to the respective functions and system architectures of each manufacturer.
These requirements are based, among other things, on established technologies and security best practices, such as cryptographic procedures as recommended by the German Federal Office for Information Security (BSI) and other international institutions. This ensures that only recognized, secured, and tested scopes are applied in future developments.
In addition, the basic technical requirements and protection mechanisms are updated with expert knowledge from the automotive industry and checked in terms of their individual application by the original equipment manufacturer (OEM). This guarantees that only the very latest mechanisms are used.
Furthermore, the automotive industry contributes to the establishment and continuous improvement of new automotive security mechanisms by way of various technical standardization bodies (e.g., AUTOSAR) or publicly funded projects (e.g., EVITA).
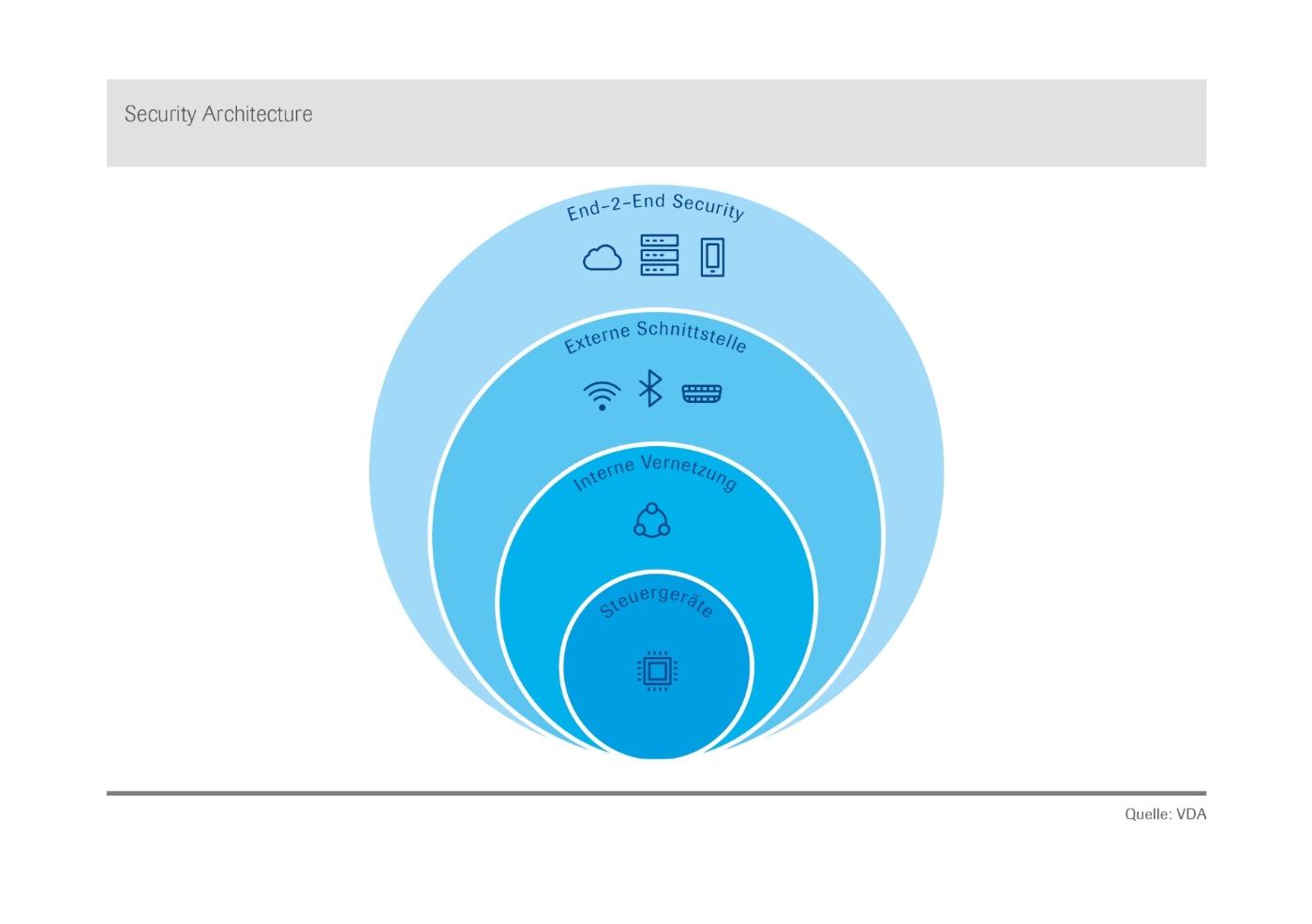
The basic technical requirements and security mechanisms are components within the framework of a holistic security architecture. This must include risk-adapted measures at the following levels within the vehicle environment:
- Individual components and control units (secure hardware and software)
- In-vehicle networking (data communication between internal systems)
- External interfaces and protocols (for example, wireless communication via mobile telecommunications or WLAN)
- End-to-end security for security-relevant services
A security architecture covers not only the vehicle itself, but also the systems involved, such as back-end or connected devices. It must take into account the functional and system-specific circumstances and requirements, and must therefore be designed specifically with these aspects in mind. This means that vehicles are not just nodes on the Internet of Things (IoT), but are usually part of a manufacturer-specific network with clearly defined rules and access.
3. Lifecycle management
Apart from the two pillars considered so far, engineering process and basic technical requirements, lifecycle management is also important, since the effectiveness of security measures can change after the development phase during the lifecycle of the product. Various external influences can lead to a drop in the security level over time. In this respect, the following circumstances, for example, should be taken into account:
- The efficacy of technical security mechanisms such as cryptographic algorithms decreases due to technical advancements (e.g., the computing power available to attackers) and general progress (e.g., the development of new analysis tools or methods).
- New vulnerabilities and attack opportunities are discovered and spread.
- New tools emerge on the hacker scene, so that initially complex and time-consuming attacks become simpler or automatable over time.
To address these challenges to product security over the lifecycle, VDA members provide for suitable and recognized measures.
One fundamental measure is field observation. This means that any attacks are identified and analyzed by technical and non-technical means. For this purpose, the automotive industry uses not only technical solutions from traditional IT but also social media, automotive-oriented web forums, or vulnerability databases to identify potential threats. The results of this field monitoring are incorporated into the security measures for newly developed products so as to continuously improve the level of protection.
Automotive Information Sharing and Analysis Center
In addition to these individual solutions, platforms have been established within the industry to enable the exchange of information on security topics such that threats can be dealt with as quickly as possible. These include the AUTO-ISAC in the USA and expert committees in the VDA. Security experts are actively involved in these platforms, as well as in research, development, and specialist conferences.
Incident Management: Organizational and technical process for responding to detected or suspected security incidents or disruptions
As a further measure, the manufacturers and suppliers of relevant components and system product security operate Incident Management to be able to react appropriately to security events. Alongside the manufacturers, the VDA is also a contact point for reporting security vulnerabilities. This information is transferred to the responsible contacts at the member companies to enable further rapid analysis and, if necessary, the initiation of countermeasures.
Classification of further approaches
The application of the three pillars of security engineering, basic technical requirements, and lifecycle management describes a holistic approach that is suitable for facing the specific requirements of networked vehicle security. As seen below, this approach has a broader scope than the demands from the political arena for certification of security measures and processes, or prescribed standard technical solutions, in conjunction with regulatory requirements.
Certification of security measures and processes
Common Criteria (CC) certification typically develops its strength in highly standardized products and regulated markets, especially in clearly defined, manageable, and distinct systems with lucid security requirements.
In contrast, vehicles are characterized by heterogeneous functionalities that evolve over time, and individual manufacturer security architectures. A certification approach for such diverse and complex systems can only cover limited aspects (and therefore not guarantee overall security), while centralized requirements inhibit innovation and increase costs, since individually optimized solutions may not be compliant.
Compulsory certification carries the risk that solutions will be designed to simply conform with a security profile, rather than to risk-adjusted measures. This would mean that the certification conveys a false sense of security but does not really improve the system security. Against this backdrop, the automotive industry does not recommend compulsory certification so as to protect the owners, drivers, and occupants of vehicles.
Demand for technical standard solutions and regulatory requirements for security measures
Standard technical solutions may provide a unified, industry-wide basis for meeting security protection needs. However, they only make sense if their security can be proven, for example, as is the case with cryptographic methods.
Industry-wide standardized solutions at system and architecture level would make it easier to scale attacks on vehicles across multiple product lines and manufacturers. Furthermore, when considering complex vehicle systems or indeed complete vehicles, it cannot be assumed that requirements for various manufacturers and models are uniform. It would also limit the pace of product innovation.
The automotive industry shares and supports the legitimate social interest that vehicles have an adequate level of automotive security. Regulatory requirements would only make sense if the goals of this regulation are not achieved by the market itself. Therefore, regulation should only define appropriate security objectives and not the technical measures themselves. The concrete solutions to attain these goals should be designed and implemented individually by the manufacturers in the context of the overall system security architecture.
The VDA and its member companies consider that the three-pillared approach adopted by the German automotive industry, as described in the sections above, is suitable for ensuring the security of vehicles and vehicle-related services. It thus requires constant improvement.





Security, Data & Digitalization
Martin Lorenz
Head of Department and Team Lead Cybersecurity & Economic Protection